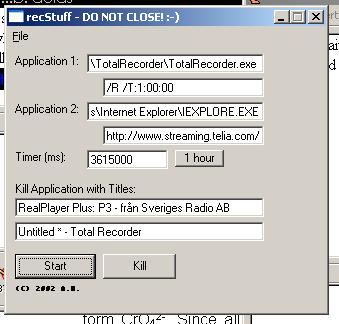
 was a small app I wrote in Visual Basic 6.0 to record radio broadcasts.
It uses a timer, the FindWindow() API call to find
applications with the given titles, and kills them. Something that can
be done on Unix in a one-liner took a whole app on Windows.
was a small app I wrote in Visual Basic 6.0 to record radio broadcasts.
It uses a timer, the FindWindow() API call to find
applications with the given titles, and kills them. Something that can
be done on Unix in a one-liner took a whole app on Windows.
- Would you rather install Windows XP (eXtra craP)?
- Uninstall all the bundled crap.
- Install any old, really legacy software first. (don't do this)
- Windows Update (do this a few times, since each time it will discover new items to update)
- Application compatibility (à la Windows XP) support:
- regsvr32 %systemroot%\apppatch\slayerui.dll
- Command Prompt tab completion (à la Unix):
- Edit HKEY_LOCAL_MACHINE\Software\Microsoft\Command Processor and change the completion character to 0x9 which is tab.
- Set up an IPSEC policy, like a firewall. See my unfinished article on Virus Experts.
- vPopmail: ./configure --enable-passwd --enable-domainquotas
- vQadmin: ./configure --enable-cgibindir=/usr/local/apache/cgi-bin --enable-passwd=y
- qmailadmin: ./configure --enable-modify-spam --enable-modify-quota --enable-vpopmaildir=/home/vpopmail --enable-help --enable-domain-autofill --enable-htmldir=/usr/local/apache/htdocs --enable-cgibindir=/usr/local/apache/cgi-bin
- php module: ./configure --with-mysql=/usr/local/mysql --with-mysql-sock=/usr/local/mysql/var/mysqld.sock --with-xml --enable-xslt --with-xslt-sablot --with-apxs2=/usr/local/apache/bin/apxs
- php fastcgi: ./configure --with-mysql=/usr/local/mysql --with-mysql-sock=/usr/local/mysql/var/mysqld.sock --with-xml --enable-xslt --with-xslt-sablot --enable-fastcgi --enable-force-cgi-redirect
- Apache: ./configure --with-ssl --enable-rewrite --enable-so --enable-suexec --disable-info --with-suexec-caller=nobody --with-suexec-uidmin=1000 --with-suexec-gidmin=1000 --prefix=/usr/local/apache2 --enable-ssl --disable-status --disable-imap --disable-asis --with-mpm=prefork --enable-auth-digest --disable-include --with-module=mappers:security
- pure-ftpd: ./configure --with-privsep --with-peruserlimits --with-virtualhosts --with-ftpwho --with-puredb --without-inetd --with-tls --with-virtualchroot --with-sysquotas
ls -1 | awk '{ print "<img src=\"" $0 "\"><br>" }' > img.html
Note that it is ls minus one, not 'l'. Basically, the rule is: awk '/pattern/ { command }' where the /pattern/ is optional. $0 will match the entire line if I'm not mistaken in my 2 minutes of experimenting with awk.
dd bs=1k skip=300 if=image.nrg of=image.iso
This will causes dd to skip 300 bs-sized bytes (300 kb) before starting the data copy. In reality, the NeRo imaGe (nrg) file is just an ISO image with a 300kb header that is *not* part of the ISO filesystem image.